Firefly States Redactor
Features
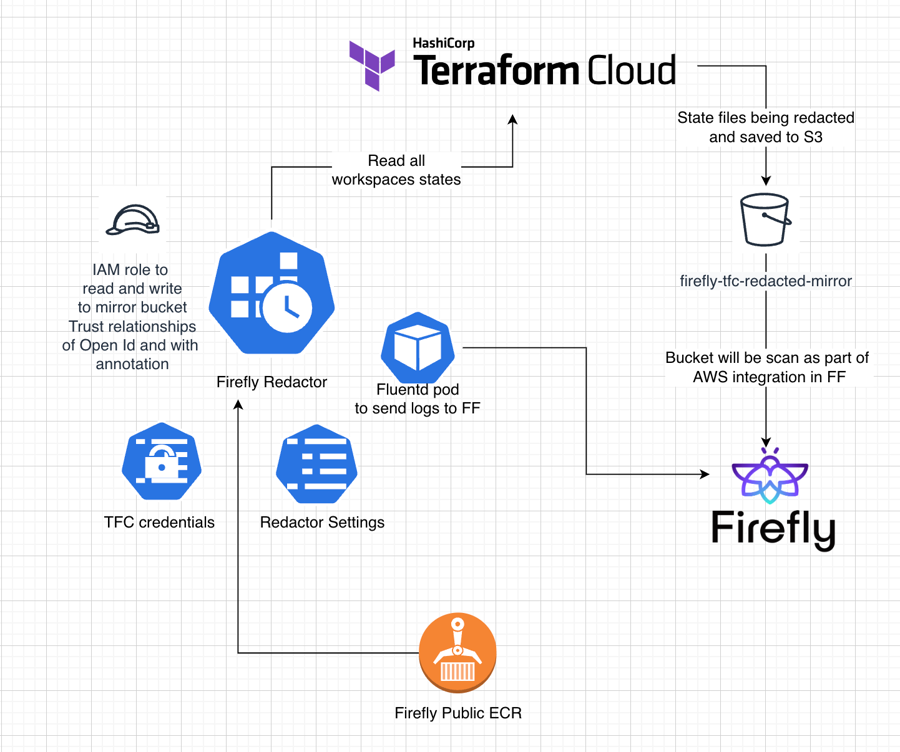
Architecture
Prerequisites
Installation (Kubernetes Helm)
Configuration Examples (values.yaml)
values.yaml)Terraform Cloud
S3 Bucket
Running on ECS (Terraform Module)
References
Need Help?
Last updated
Was this helpful?